Why CyberBunker Was Blacklisted By Spamhaus
On Wednesday we witnessed the real power of cyber-attacks when the anti-spam organization Spamhaus was hit by a number of large-scale distributed denial of service (DDoS) attacks, which not only brought down their own website temporarily, but also a caused a widespread disruption across the Internet. The DDoS attacks flooded targeted websites with extraordinary amounts of dummy traffic, making them unreachable by internet users trying to access them, and slowing down internet speeds worldwide.
Spamhaus was allegedly targeted in retaliation by the Dutch web hosting company CyberBunker, who are rumoured to host spam, phishing sites, and malware. Spamhaus blacklisted CyberBunker from sending out these emails, bringing on the attack.
But what is phishing, and how does it facilitate data breaches?
“Phishing” is an email fraud attempt that targets both individuals and organizations, seeking unauthorized access to confidential data. Phishing emails appear to come from a trusted source and contain links or attachments, which when opened, give the hacker instant access to the recipient’s computer and/or internal network. The email usually contains key information, like sender contact information, or bank details, to make them appear legitimate.
There are also phishing websites, which CyberBunker was rumoured to have hosted. The hacker provides a fake URL to the victim, which redirects them to a phishing website that solicits private data. This website is often engineered with a look-alike URL (e.g., replace “I” with “l”). Alternatively, the phishers can use browsers to display the real URL but phish content (e.g., xss iframe phishing), making the phishing scams virtually undetectable by the average user. This is the type of activity that Cyberbunker allegedly hosted on their servers, which led to their blacklisting by Spamhaus.
The Global Impact
Roughly 156 million phishing emails are sent globally every day. Most are destroyed in spam filters, with around 8 million emails making it into peoples’ inboxes. Phishing emails on their own are not harmful – the real issue comes from clicking on suspicious links, or opening suspect attachments. Roughly 80,000 people end up falling for phishing scams every day. Phishers will try to gather things like banking information, credit card numbers and passwords, which can result in identity theft, credit card fraud, financial loss, and other Internet scams.
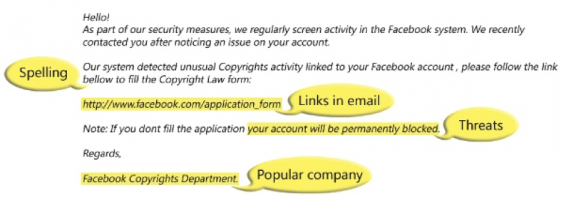
What does a phishing email look like?
Example 1:
Example 2:
Reduce Your Risk
Both businesses and individuals can reduce the risk of falling victim to phishing and malware attacks by doing the following:
- Be alert. Holiday distractions and office closures make certain times of the year more convenient for hackers.
- Educate employees, particularly bookkeeping staff who have access to key banking information, on fraud prevention.
- Even if you recognize the email sender, don’t click on a link or attachment unless you can verify it or were expecting it.
- Monitor activities in all bank accounts closely and regularly.
- Contact your bank immediately through a verified number or in person if you have any problems accessing bank accounts online.
- Implement restricted privileges to computer users that will limit their ability to download software without an administrator’s permission.
- Ensure your anti-virus, spyware and firewall protection is updated regularly.
- Identify the digital assets that are at most risk to intrusion and segregate them to provide additional security.
- If you do experience a security breach, report it immediately to the FBI Cyber Crime Division and Internet Crime Complaint Center (US) or the Canadian Anti-Fraud Centre (Canada). Then call a reputable computer technician for assistance.
- Always have more than one computer backup, which is physically removed from the network, in case this is also compromised. Virtual data rooms are a great option.
Data rooms are a cloud-based secure document sharing solution. Online data rooms comply with the latest industry standards for data security, provide bank-grade data encryption and granular user permissions to manage who has access to critical documents, even after they have been downloaded.
Firmex is a cloud-based virtual data room solution that facilitates secure document sharing across corporate firewalls. Our data rooms are used for highly confidential transactions seen with M&A, Corporate Finance, and Procurement, as well as Regulatory Compliance and Governance processes. To learn more about the security benefits of a virtual data room, visit Firmex.